What happened
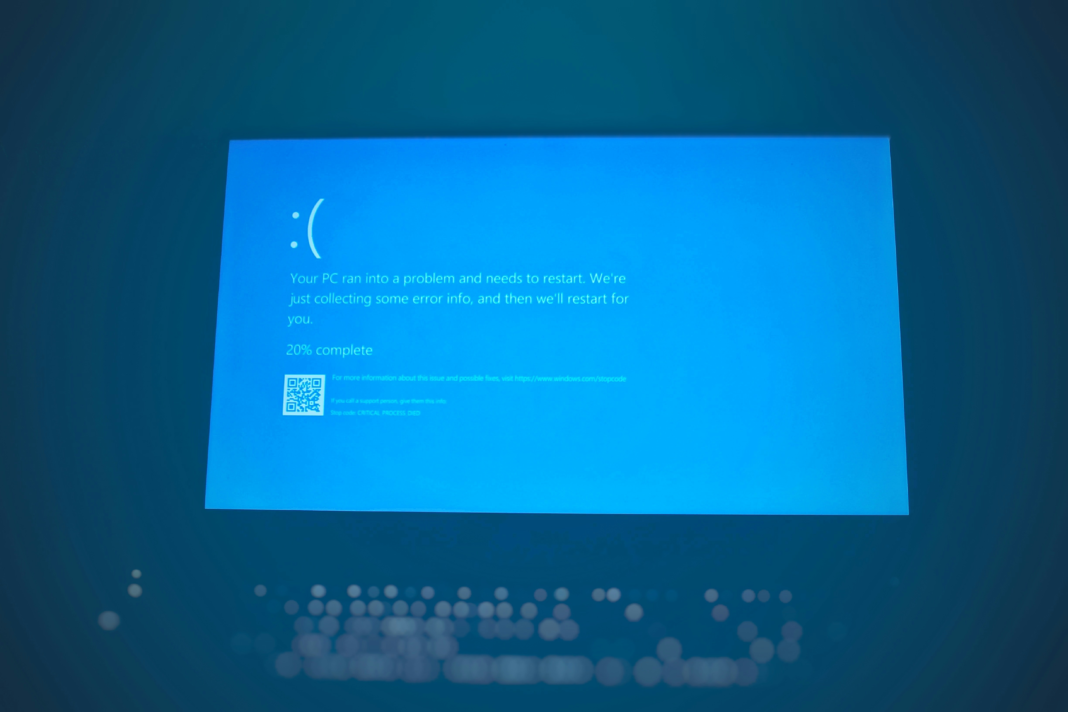
The ClickFix attack uses fake Microsoft Windows Blue Screen of Death (BSOD) screens to trick users into executing malware. The campaign targets hospitality organizations across Europe and impersonates Booking.com reservation cancellation notices. Victims are redirected to cloned Booking.com pages where a fake BSOD instructs them to paste a malicious command into the Windows Run dialog. This installs DCRAT, a remote access trojan that enables persistent access, credential theft, and system control while evading endpoint defenses.
Who is affected
Hospitality employees handling booking cancellations and customer service communications are the primary targets.
Why CISOs should care
Highly convincing social engineering combined with system spoofing can bypass security controls and result in full endpoint compromise.
3 practical actions
1. Reinforce phishing training: Educate staff to recognize fake BSOD prompts and impersonation tactics.
2. Restrict command execution: Limit user permissions to prevent execution of unauthorized scripts or commands.
3. Monitor endpoint behavior: Detect abnormal PowerShell usage, .NET compilation, and persistence techniques.