Security operations centers have embraced artificial intelligence to reduce alert fatigue and accelerate investigations, but trust in automated decision-making remains uneven. Many organizations have discovered that while AI can process alerts faster, precision and accuracy, particularly avoiding wrong verdicts and hallucinations, remain the most critical requirements, followed by consistency and explainability needed for security leaders to confidently operationalize it.
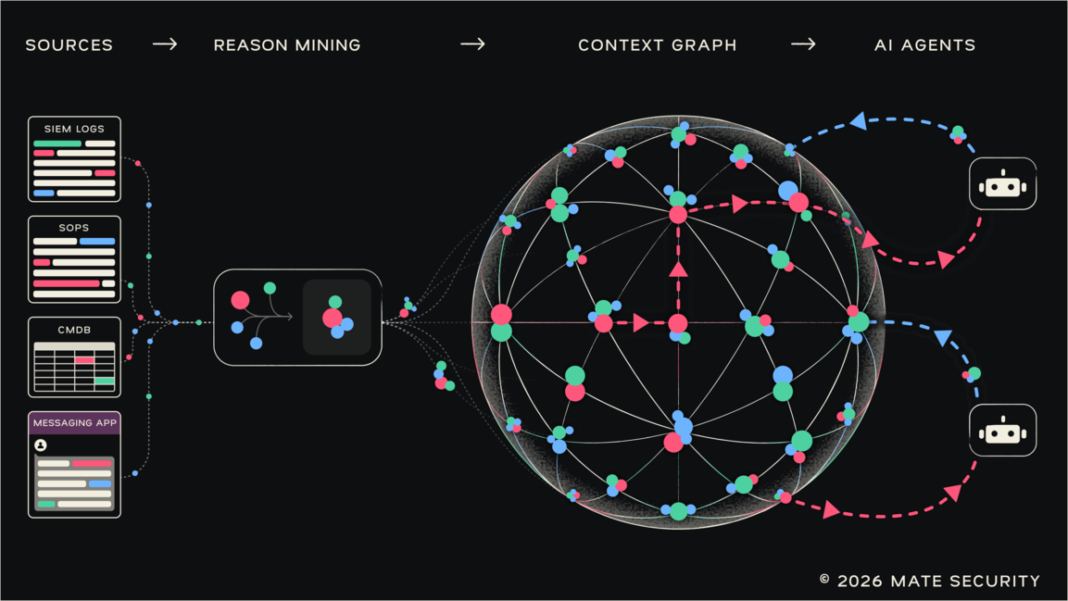
Mate Security believes the issue isn’t AI capability, but also the structure of the data powering it. The company recently introduced the Security Context Graph, a foundational architecture designed to help AI SOC agents reason using operational context rather than isolated alerts and logs.
The announcement reflects a broader industry shift toward agentic AI, where automation tools move beyond assisting analysts and begin making or recommending decisions independently. Yet early SOC AI deployments have exposed a common weakness: agents often lack the contextual awareness that experienced analysts rely on when investigating threats.
“We are witnessing the AI SOC revolution as we speak,” said Asaf Weiner, Co-Founder and CEO of Mate Security. “AI is slashing alert queues, increasing focus, and speeding up SOC work like never before. Overloaded Tier-1 analysts are being elevated to AI engineers. They are happier!”
Despite those improvements, Weiner says many CISOs remain cautious about trusting AI to operate or even make sensible recommendations within high-stakes security environments.
“When I meet a CISO for the first time, I can feel the mistrust,” Weiner said. “They have piloted AI in their SOC and were burned with a bad experience: agents taking months to learn, confidently generating wrong verdicts, and requiring more ‘babysitting’ than the SOAR they were meant to replace.”
Turning Analyst Knowledge Into Structured Intelligence
Traditional SOC workflows organize data around alerts, logs, and documentation that are primarily designed for human interpretation. Analysts rely heavily on institutional knowledge, experience, and situational awareness to interpret this information and connect signals across systems. AI, however, typically lacks access to that reasoning layer.
Mate Security developed the Security Context Graph to capture and structure that missing layer of operational intelligence. Rather than treating investigations as static outputs or rule-based playbooks, the graph transforms fragmented organizational data into contextual memory to preserve how and why analysts reach conclusions during investigations.
“AI agents are fed data structured for humans,” said Weiner. “SOC analysts work with tables, logs, and documents… they rely on their experience and common sense to connect the dots. But AI cannot do that. AI agents need more than the ‘what’, they need the ‘why’: the operational context.”
The graph continuously maps relationships across policies, asset ownership, historical investigations, and organizational workflows. AI agents can then navigate these relationships to support more consistent and transparent security decisions.
“This is why we have built the Security Context Graph,” Weiner said. “The underlying foundation for our agentic AI platform.”
Building Predictability Into Automated Investigations
According to Mate Security, organizations deploying AI agents powered by the Security Context Graph are seeing measurable operational improvements across several core SOC functions.
The company says agents demonstrate stronger accuracy by analyzing investigations through contextual reasoning rather than rigid rule enforcement. The graph also serves as a unified knowledge layer, reducing conflicts between multiple data sources, a persistent challenge in many enterprise security environments.
Transparency is another focal point. Mate Security says agents can articulate their reasoning in plain language, providing analysts and leadership teams with greater visibility into how conclusions are reached. The architecture also enables agents to flag uncertainty when data gaps exist, helping prevent overconfident automation.
“The Security Context Graph is a living and breathing structure,” said Weiner. “It is dynamically rebuilding and optimizing with every investigation, every ownership change, every policy change, so decisions are made according to what’s relevant right now.”
Notably, Mate Security built the graph before launching its AI agents, taking what the company describes as a deliberate data-first approach to agent development.
“Agents are only as effective as the data structure on which they are built,” Weiner said. “This is the only way for AI to earn trust.”
The company says the Security Context Graph has served as the backbone of its AI SOC agents since its earliest enterprise deployments. The public unveiling offers insight into the proprietary architecture that has supported agent accuracy and consistency from the start.
Security Teams May Need Memory, Not Just Automation
As security operations become more complex and resource-constrained, the industry is increasingly shifting its focus from simply accelerating investigations to improving the quality and reliability of security decisions. While automation has reduced manual workloads, the next challenge is preserving institutional knowledge in ways that scale with the growing threat landscape.
Mate Security’s Security Context Graph reflects a growing recognition that effective AI in the SOC requires more than processing power. By translating analyst expertise into continuously evolving contextual intelligence, the company is betting that the future of AI-driven security will be defined not just by faster responses, but by decisions organizations can confidently trust.