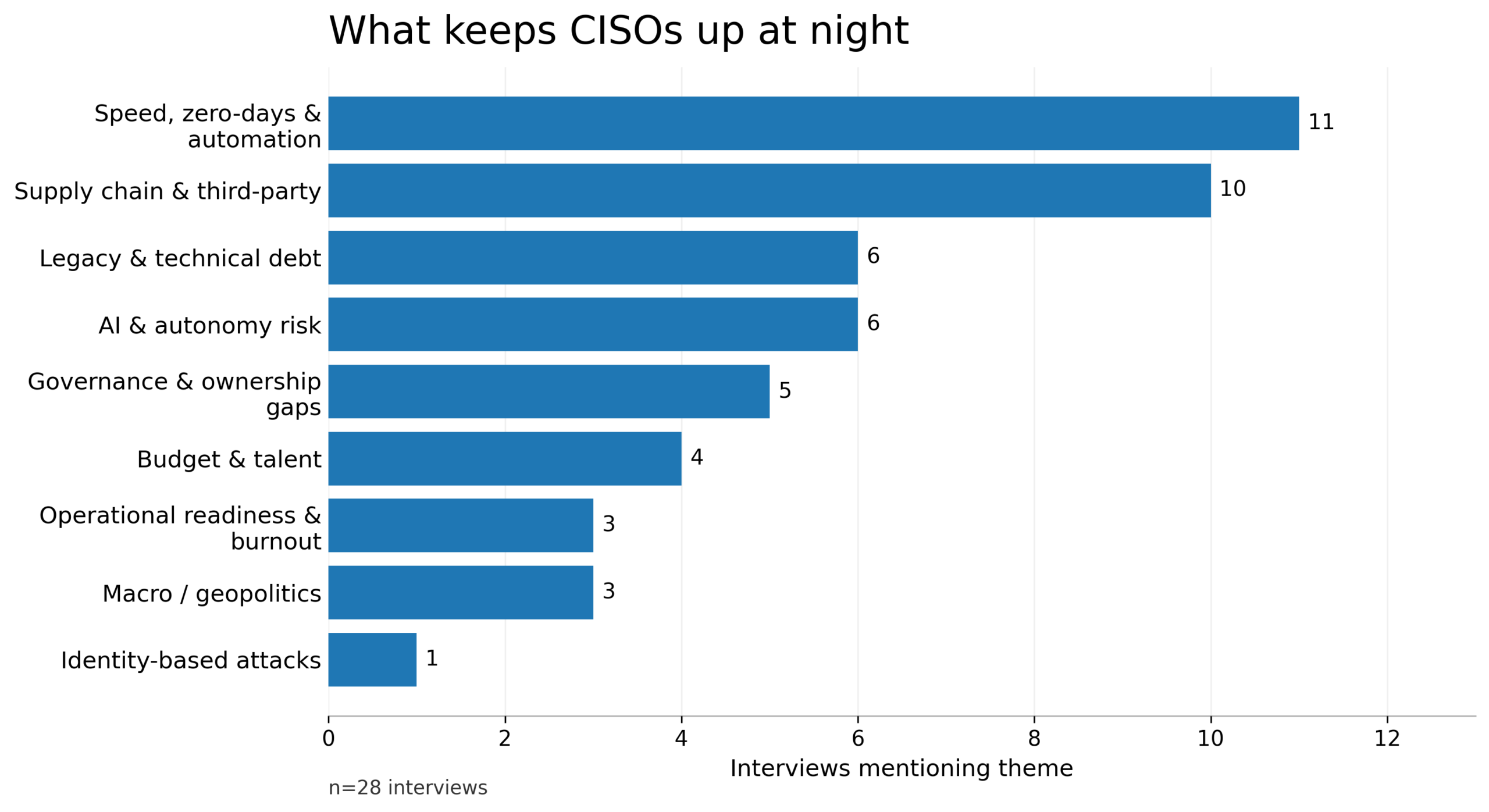
Across 28 CISO Diaries interviews, the most consistent signal wasn’t a new buzzword, a new vendor category, or a single “silver bullet.” It was a set of recurring constraints, speed, complexity, dependencies, integrity, and the leadership patterns that reliably outperform them.
This report is not a survey. It’s a synthesis of operator thinking: what CISOs repeatedly return to when asked what matters, what breaks, what’s changing, and what they’re building for next.
1) The perimeter is no longer where trust is decided
Perimeter thinking doesn’t vanish overnight, it simply becomes less useful with every workflow that runs through SaaS, APIs, identity brokers, and third parties. The control plane has moved to identity and authorization, and the interviews reflect that shift with unusual directness.
“The idea that we can protect a company by guarding the network edge is already outdated.” – Einat Shimoni
If the perimeter is fading as a primary line of defense, what replaces it is not “zero trust” as a slogan, but identity as a production system: visibility into who and what can access critical resources, how privilege accumulates, and how quickly abnormal access can be contained.
2) Supply chain and third-party risk is the ambient threat model
In these interviews, third-party exposure isn’t treated as a procurement sidebar. It shows up as a first-order concern: the reality that modern organizations are dependency graphs with unclear edges, and that compromise increasingly arrives through paths nobody is monitoring in real time.
“Supply chain risk and the rise of automated attacks on open-source supply chains…” – Derek Galvin
As ecosystems expand, vendors, managed services, SaaS tooling, open-source components, the attack surface is no longer something a single team can “cover” through effort. What matters is whether the organization can maintain a living understanding of trust relationships, enforce least privilege across integrations, and detect unexpected behavior across dependency paths before damage becomes systemic.
3) AI shifts the conversation from detection to integrity
AI is not entering the security story as another tool. It’s entering as an accelerant: for attackers, for defenders, and for the business itself. Several interviews frame the next phase not as “AI risk” in the abstract, but as a deeper challenge: proving what’s real, what changed, and what to trust.
“We are moving from protecting confidentiality to protecting integrity… the CISO’s job will be to verify reality.” – Alexander Raif
This is where a subtle reframing happens. Traditional security asked, “How do we keep intruders out?” The emerging question is, “How do we verify outcomes and intent in environments where content, actions, and even decisions can be synthesized at scale?”
In 2026, integrity becomes a primary asset class: the integrity of transactions, the integrity of identity, the integrity of decisions made by automated systems, and the integrity of the data those systems use.
4) Speed is the meta-capability
Many risks are not novel. What’s novel is the pace: attackers scale and adapt quickly; internal complexity expands quickly; technology adoption outpaces governance. A growing portion of security success becomes temporal: how fast can you notice, decide, contain, recover, and learn?
“Speed. Attackers scale and adapt faster than many organizations can decide.” – Tim Sattler
This idea also shows up in the implied failure modes: delayed decisions, slow coordination, unclear authority, and incident response that becomes improvisation. The CISOs who sound calm are rarely the ones who claim perfection; they’re the ones who’ve designed for reality, ambiguity, incomplete data, competing priorities, and built decision loops that hold up under pressure.
5) “Boring controls” compound, if they’re actually executed
The interviews repeatedly return to fundamentals: visibility, access control, secure configurations, validation, and response readiness. Not because CISOs are conservative, because fundamentals have the highest compounding return.
“Flashy tools come and go. Boring controls, executed well, compound.” – Jason Loomis
The emphasis is not on collecting controls but on operationalizing them: coverage you can prove, changes you can detect, and failures you can contain. This is also where many interviews hint at a quiet standard for maturity: can the organization demonstrate that its security posture holds under stress, rather than describing it in documentation?
6) Culture and incentives are a security control
One of the sharpest themes across the series is that the most expensive security failures often aren’t caused by a lack of technology, they’re caused by mismatched incentives, unclear accountability, and friction that teaches teams to route around controls.
“You can’t ‘security your way out’ of bad incentives.” – Einat Shimoni
The leaders who describe real traction talk about making security legible and adoptable: not simply “training,” but shaping how work is done by default, reducing cognitive load, and ensuring people understand why the secure path exists, and how to take it without burning time and attention.
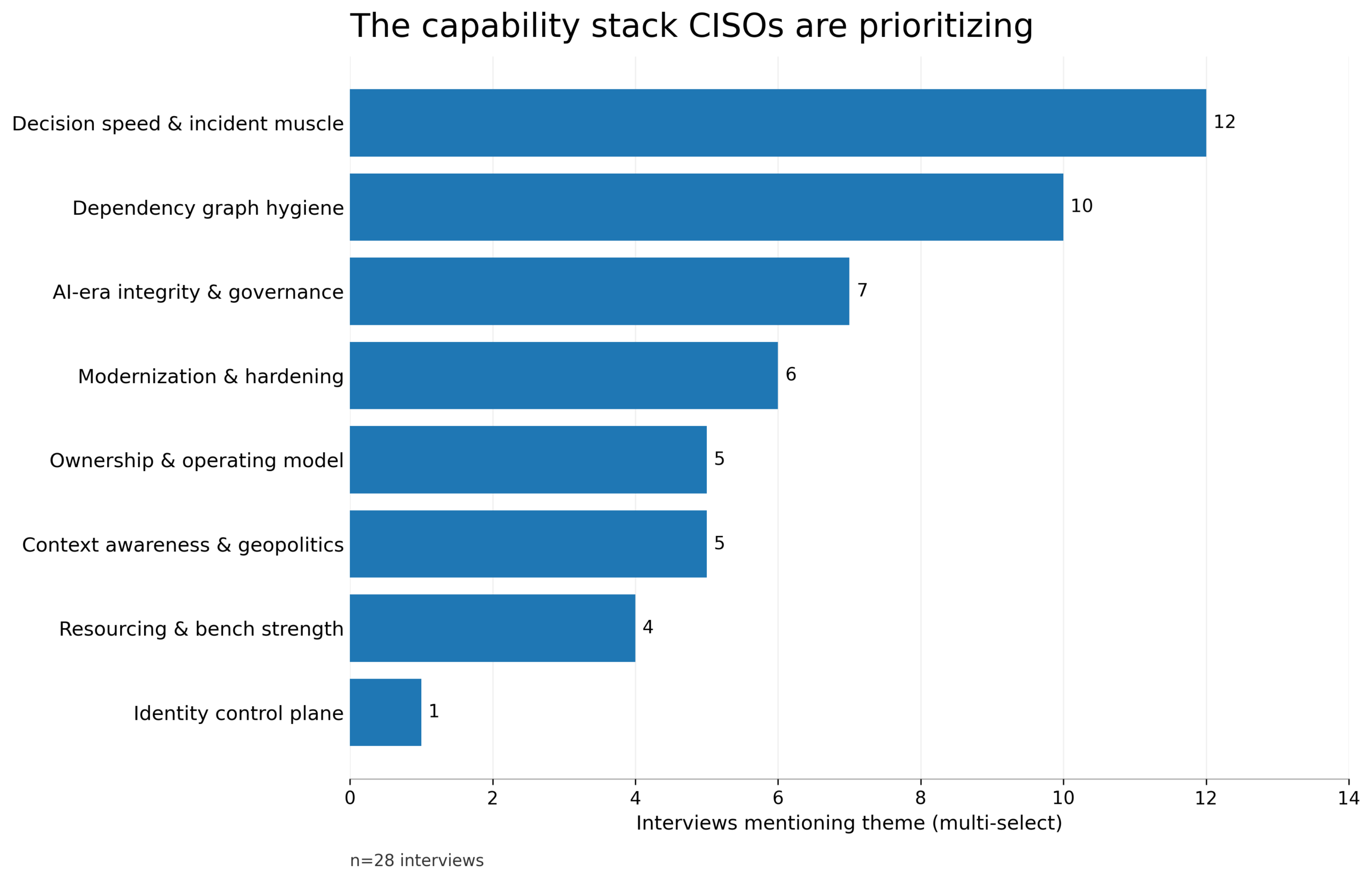
7) The future security team is a supervision and assurance layer
A recurring future-state picture emerges: security teams spending less time on repetitive mechanical work, and more time supervising automation, validating integrity, and managing AI-driven systems, both defensive and adversarial.
“We’ll basically be the referees in a robot wrestling match.” – Peter Egyed
The implication is not that humans disappear. It’s that the human role becomes higher-leverage: setting constraints, deciding what “good” looks like, validating outcomes, and responding to exceptions. In that world, the differentiator is not raw headcount; it’s how well an organization designs its automation and verifies its behavior.
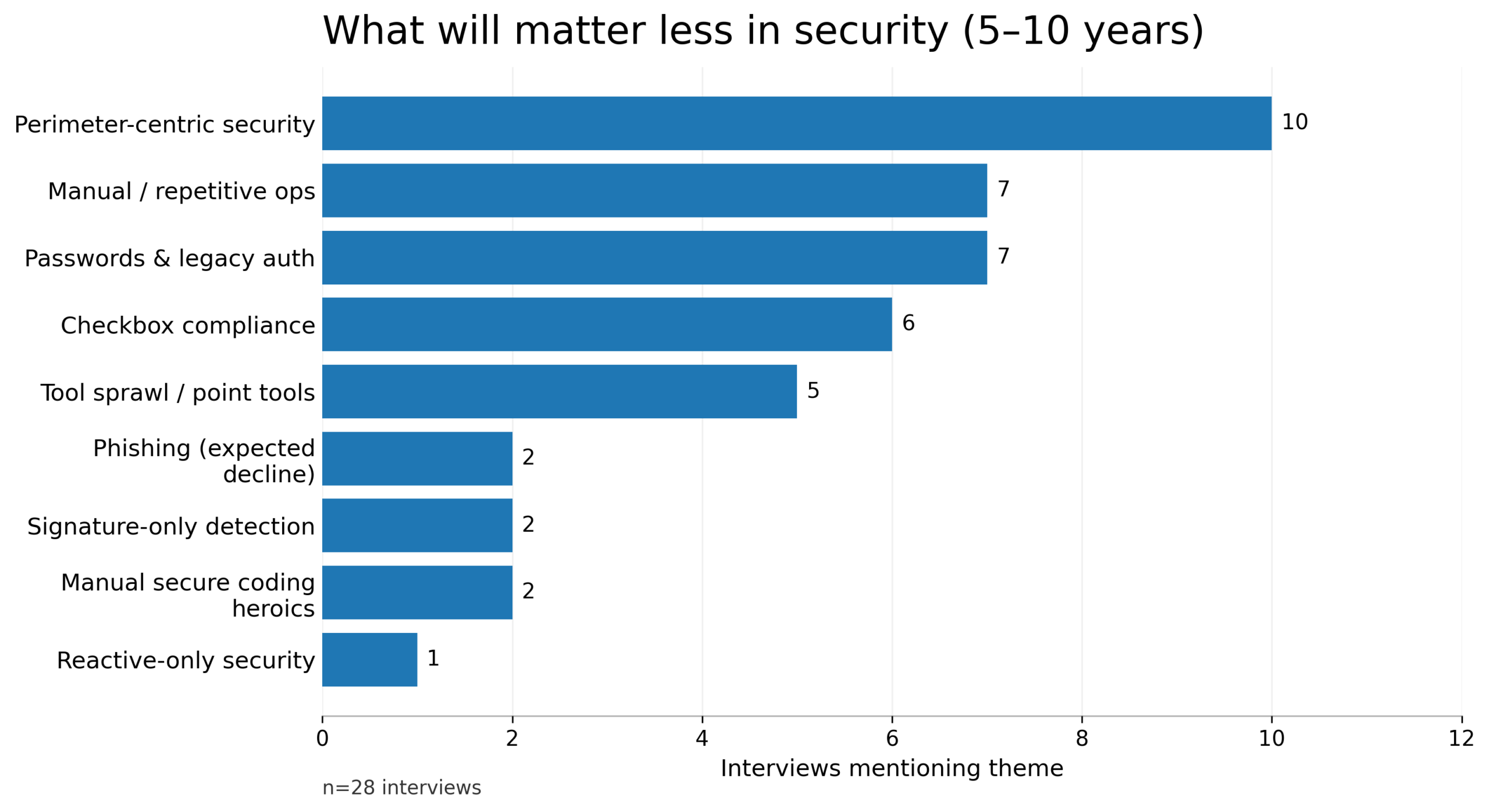
8) What will matter less: perimeter mythology, passwords, and manual toil
When CISOs talk about the next 5–10 years, a few declines show up consistently: perimeter-centric security, password dependence, manual repetitive operations, and checkbox-first compliance approaches that don’t reduce real risk.
“Perimeter-based security thinking… is already outdated.” – Kim Bruland
This isn’t optimism. It’s prioritization. It reflects a belief that the most valuable security work will migrate toward: identity and access control as infrastructure, continuous validation, and faster recovery from inevitable failure.
The 2026 Priorities on One Page
If the point of a report is a usable distillation, here is the simplest accurate version of what the interviews collectively emphasize:
- Treat identity as the control plane. Access, privilege, and authorization, not network location, now determine trust and risk.
- Design explicitly for dependency risk. Security posture is shaped by suppliers, SaaS platforms, open-source components, and integrations as much as internal systems.
- Protect integrity as a primary security objective. The ability to verify data, decisions, and system behavior becomes foundational in AI-mediated environments.
- Build decision speed as a core capability. Detection, containment, and recovery speed consistently determine real-world security outcomes.
- Execute fundamentals with provable coverage. Visibility, access control, secure configuration, validation, and response readiness deliver the highest compounding return.
- Align incentives so secure behavior is the default. Controls are only effective when ownership, accountability, and workflows reinforce adoption.
- Evolve security into a supervision and assurance function. Security teams increasingly validate automation, monitor system integrity, and manage exceptions rather than perform repetitive manual tasks.
- Move away from perimeter-centric and manual security models. Static perimeter defenses, password dependence, and manual operational toil continue to decline in effectiveness and relevance.
The Composite Signal
The most useful way to read these interviews is not as individual profiles, but as a composite signal.
In 2026, security “moves the needle” when it stops trying to win by accumulation, more tools, more alerts, more policies, and starts winning by design: fewer unknowns, clearer ownership, faster decision loops, and systems that can be verified under pressure.
The future described here isn’t utopian. It’s simply more honest: compromise happens, dependencies fail, AI changes the texture of reality, and speed decides outcomes. The question is whether your organization is built to recognize that truth early, and recover fast enough to keep compounding anyway.

